Lesson
Plan Title: How to
Bypass Client Side JavaScript Validation
Concept /
Topic To Teach:
Client-side validation
should not be considered a secure means of validating parameters. This
validation only helps reducing the amount of server processing time for normal
users who do not know the format of required input. Attackers can bypass these
mechanisms easily in various ways. Any client-side validation should be
duplicated on the server side. This will greatly reduce the likelihood of
insecure parameter values being used in the application.
General
Goal(s):
For this
exercise, the web site requires that you follow certain rules when you fill out
a form. The user should be able to break those rules, and send the website
input that it wasn't expecting.
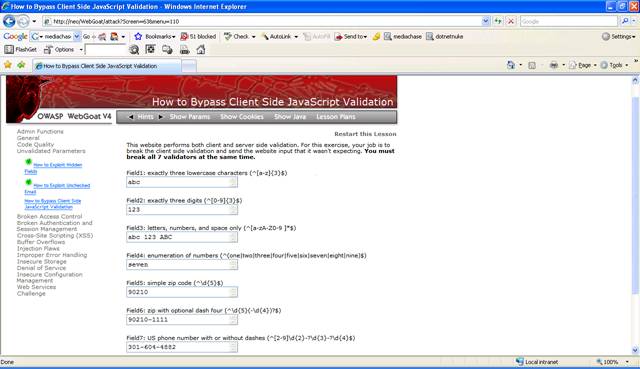
Figure 1 Lesson 6
There are two
ways to complete this lesson. The first one is to submit a valid request like
the one from the screenshot above and intercept this using WebScarab. The
second way is to intercept the HTTP Response when loading the page and remove
the Javascript that validates the values.
Solution 1
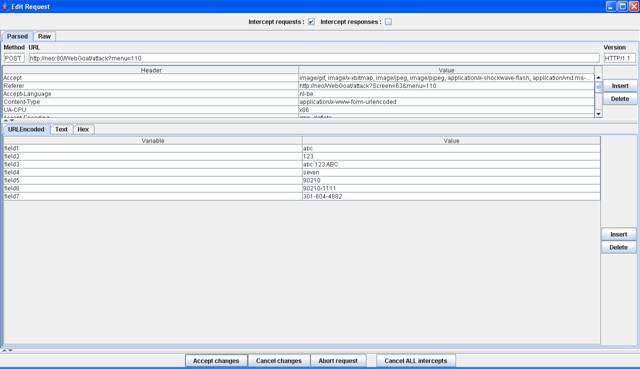
Figure 2 Intercept request
Add different
symbols to the fields and click "Accept changes".
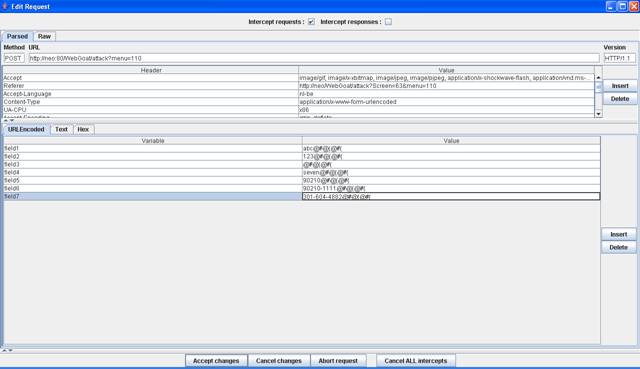
Figure 3 Change parameters
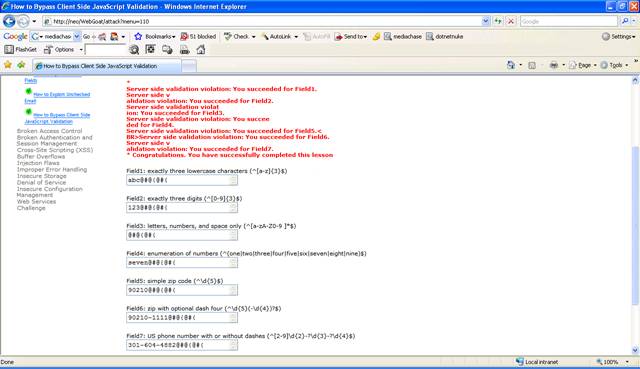
Figure 4 Lesson 6 Completed
Solution 2
Reload the
page by clicking on the menu item "How to bypass Client-Side Javascript
Validation" and intercept the response in WebScarab.
![]()
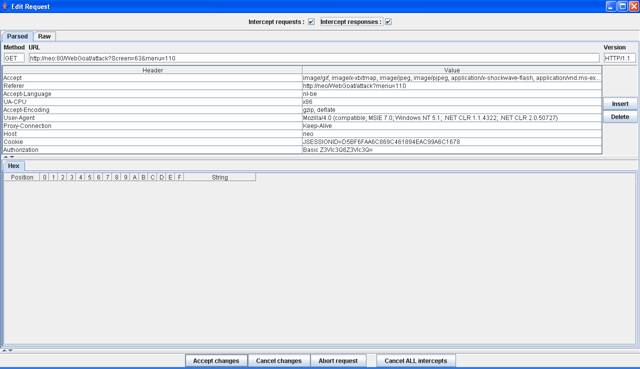
Figure 5 Enable "Intercept responses"
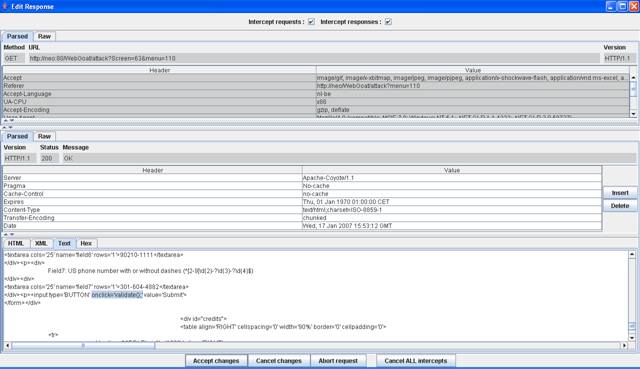
Figure 6 Intercepted response
If you remove
the onclick="validate();" the "Submit" button will not work anymore.
Locate the
validate() Javascript function in the HTML page.
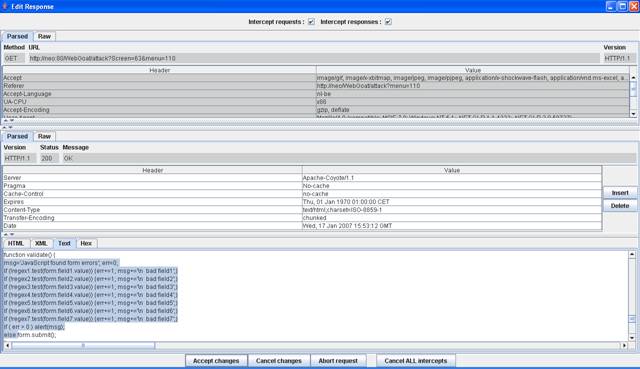
Figure 7 The function validate()
Removing the regular
expressions will remove the Javascript validation and submit the form.
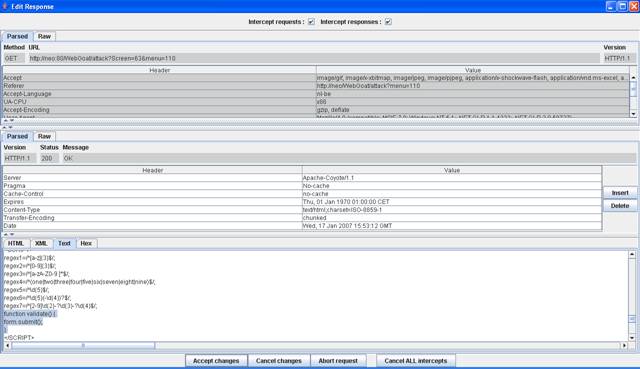
Figure 8 Changed validate() function
Click "Accept
changes". This returns a HTML page like before but without any regular
expression checks.
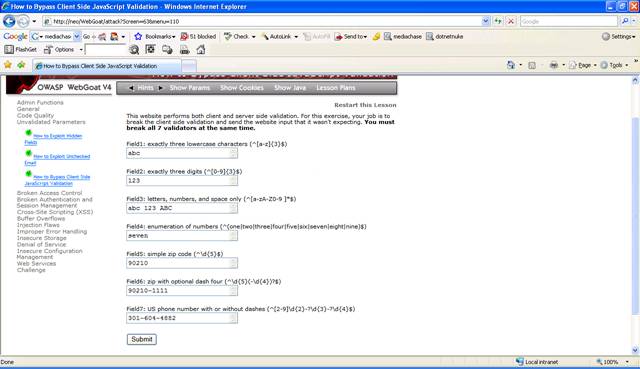
Figure 9 It looks the same
Change the
fields in the HTML page to contain symbols like @#@@# and click "Submit".
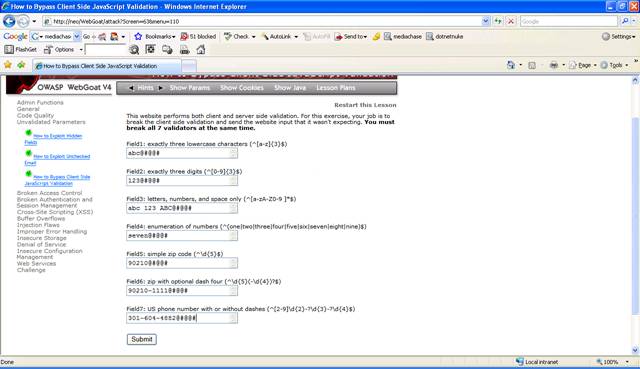
Figure 10 No more regular expression checks
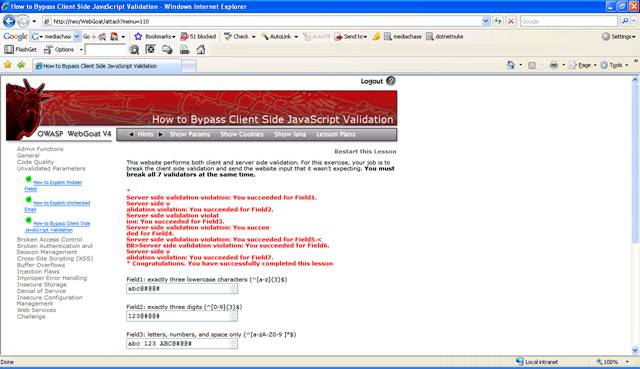
Figure 11 Lesson 6 Completed
