Lesson
Plan Title: How to
Exploit Hidden Fields
Concept /
Topic To Teach:
Developers
will use hidden fields for tracking, login, pricing, etc.. information on a
loaded page. While this is a convenient and easy mechanism for the developer,
they often don't validate the information that is received from the hidden
field. This lesson will teach the attacker to find and modify hidden fields to
obtain a product for a price other than the price specified
General
Goal(s):
The user
should be able to exploit a hidden field to obtain a product at an incorrect
price.
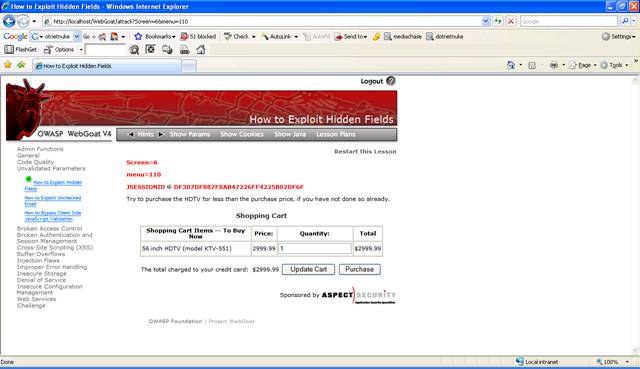
Figure 1 Lesson 4
Solution:
To change the
hidden field you need to start your favorite HTTP Interceptor. You can use
WebScarab from OWASP to intercept the request and change the hidden field.
Configure your browser to use a local proxy. In Internet Explorer you can do
this via "Tools" – "Internet Options" – "Connections" – "LAN Settings". You
must define proxy "localhost" with port 8008.
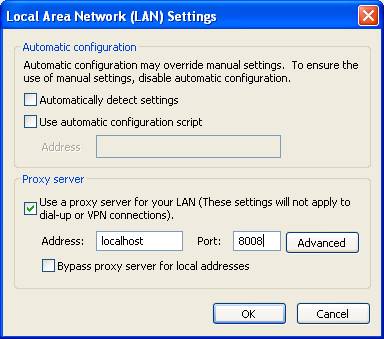
Figure 2 Set local proxy in Internet Explorer
Start
WebScarab
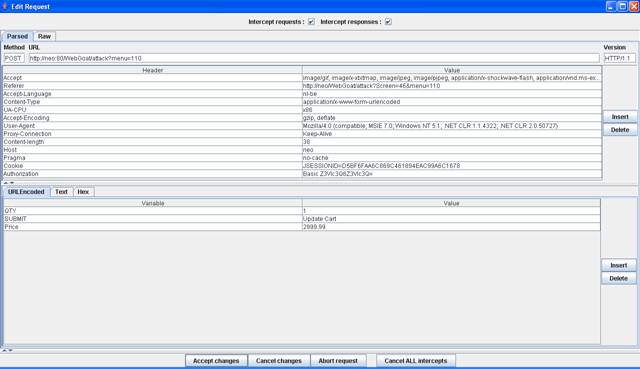
Figure 3 Intercept request with WebScarab
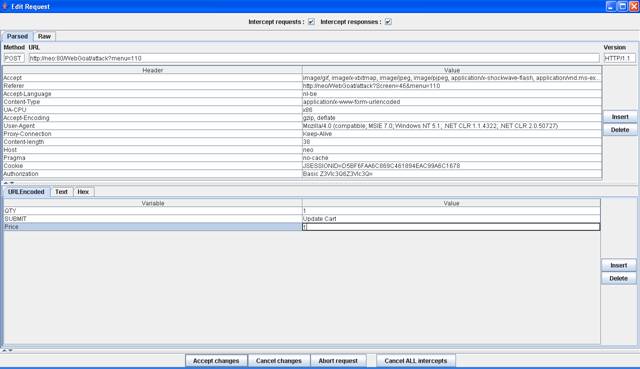
Figure 4 Change the Price variable to 1
Figure 5 Lesson 4 Completed
