Lesson
Plan Title: How to Perform Numeric SQL Injection
Concept /
Topic To Teach:
SQL injection attacks represent a serious threat to any database-driven site. The methods behind an attack are easy to learn and the damage caused can range from considerable to complete system compromise. Despite these risks, an incredible number of systems on the internet are susceptible to this form of attack.
Not only is it a threat easily instigated, it is also a threat that, with a little common-sense and forethought, can easily be prevented.
It is always good practice to sanitize all input data, especially data that will used in OS command, scripts, and database queries, even if the threat of SQL injection has been prevented in some other manner.
General
Goal(s):
The form below allows a user to view weather data. Try to inject an SQL string that results in all the weather data being displayed.
Solution:
The
application is taking the input from the select box and inserting it at the end of a pre-formed
SQL command.
Compound SQL
statements can be made by joining multiple tests with keywords like AND and OR.
Try appending a SQL statement that always resolves to true.
This is the
query: SELECT * FROM weather_data WHERE station = 101
Intercept the post request with WebScarab and replace 101 with 101 or 1=1!
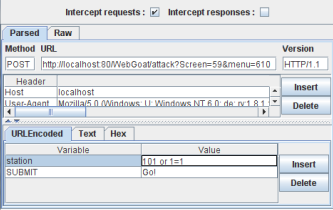
Figure 1 Intercepted Request with WebScarab
As the SQL Statement is true for every station you get
a list of all stations:
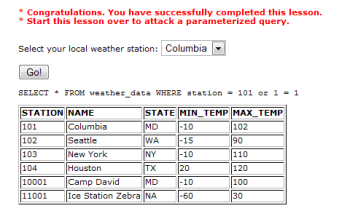
Figure 2 All stations are visible
